 Caveat: I am not a developer so what I am about to reveal may or may not be news to the developer community. Nevertheless, this is not something that I was aware of previously and I have not seen any mention of this in the media that I subscribe to (which is a fairly broad cross section of the online press).
Caveat: I am not a developer so what I am about to reveal may or may not be news to the developer community. Nevertheless, this is not something that I was aware of previously and I have not seen any mention of this in the media that I subscribe to (which is a fairly broad cross section of the online press).
Further, to my knowledge this is not something that has been specifically authorized by me in the course of my use of either my computer or the software on it or my iPhone and the software running there. I did not grant permission for this information to be transferred anywhere and I did not ever to my knowledge see any request to allow this information to be collected much less shared and shared without my knowledge.
Here’s the deal. Today I was going through the console on my Mac Book Pro trying to see if I can figure out why it suddenly won’t display anything on the screen (I was doing this using LogMeIn since I could not work on the computer locally since the display has apparently died.
During the process of digging through the console to see if there was any obvious cause for the completely unexpected display failure I came across something that I found as unexpected as the aforementioned problem and which I (and possibly other iPhone owners) will find very disturbing.
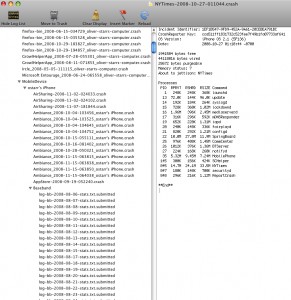
As you can see, this is a snapshot of my console log file. It shows some surprising information – at least from my perspective. Unless I am completely misinterpreting this information it looks as if the iPhone is logging everything that happens to it and I mean everything, from usage stats on the baseband to which applications are installed, when they are used and when they malfunction, and then, when you connect your iPhone to iTunes the phone downloads all this information to your console where it is logged. Further, judging from the text adjacent to the baseband logging details this information has been “submitted”.
This begs the question: SUBMITTED WHERE???
Again, I wasn’t asked if I wanted this information collected and I sure as hell wasn’t asked if I wanted it submitted either. If I am correct and what is going on here is that without my prior knowledge let alone my consent this data is being transmitted back to Apple for their own purposes (after all with literally hundreds of crashes of the mobile Safari browser on this iPhone alone, if the data were being used for my benefit someone would have contacted me don’t you think?) using my computer to collect the data and my Internet connection to transport it.
When a Microsoft application crashes and the crash reporter wants to send information back to Microsoft they have the courtesy to ask your permission. They also take time to explain in writing what is being sent to them and what is being done with it. They make certain guarantees at this time as well about personally identifying information and how that data is to be used.
I fail to see where such courtesies are being extended to me by Apple. I fail to see an explanation as to what is being collected, whether or not it is personally identifying or what Apple intends to do with this information once they’ve managed to snoop it from my phone and computer.
Frankly I think this is outrageous. The fact that this data is being collected at all without requesting permission to do so is bad enough. The fact that it appears to be sent via clandestine transmission to Apple without any prior disclosure seems to be a criminal trespass based upon my understanding of the privacy laws in this country.
This strikes me as a grotesque abuse of my trust. What if I had personal medical information stored on my phone? At this point how would i know who at Apple had accessed this information or with whom it had been shared – again all without my knowledge or consent.
Since when did owning a mobile phone void one’s right to privacy or exempt a company from the need to disclose their data collection policy? When did Apple wake up and decide that it was okay to spy on their customers in this truly repulsive fashion?
Now, as I said at the outset of this post, I am not a developer so it is possible that either this is something that has previously been discussed and I am late to the party – it is also possible that I am misunderstanding something about these console log statements and that what I think is going on really isn’t.
However, on the off chance that I am neither late to the party nor misunderstanding these log files then this is a real issue that deserves some real attention. I sincerely doubt that I am alone in feeling completely raped by Apple’s data collection policies and the fact that I don’t appear to have been included in the decision making process about which data will be logged, collected and reported regarding my use of a device that I bought and paid for and for which I have not in any obvious way been notified of zero privacy nor authorized anyone to keep tabs on my beyond my approval for AT$T to track my usage of their network for billing purposes.
Is this grounds for a class action? I’ll let the lawyers tell me the answer. Is this grounds for a consumer-company smackdown. I think it is. If what I think is going on is really going on then it’s time to put Apple in its place. The back door was bad enough but this latest is simply egregious.

Pingback: iPhone Phones Home, Tells Everything
Pingback: iPhone Phones Home, Tells Everything | StarrTrek
Pingback: Evidence of iPhone privacy breaches? | Signal to Noise
Pingback: Possible iPhone personal privacy breaches?
While you are right to be angry, you should also make sure that the logging of this information is covered under the End User License Agreement that you “signed” when you activated your iPhone via iTunes. If anything, you would find the answers to you questions there, and from that point have only yourself to blame in it being stated there and you not knowing.
And yes, I know many people don’t read those. But this is a reason why you should.
@ARJ
Your point would be good if I had activated my device via iTunes, however I along with millions of others activated my iPhone 3G at an Apple store.
During the activation process I did sign a document – the new two year contract required by AT$T for service provisioning to this particular locked device – I read it as well – and unless I missed a major term in the agreement there was nothing in it that authorized Apple to log information about applications, performance or content on my phone, transfer these logs to my computer during the synchronization process, store this information on my computer without my knowledge (and also without my consent), and then again without my knowledge or permission, utilize my Internet connection to transfer this data to Apple.
As I stated in a prior post concerning the backdoor that Apple clandestinely placed in the device to allow them to shut down “malfunctioning” applications if Apple felt that allowing (or more to the point creating) these methods of access and information retrieval was really of benefit to the end user then why did they attempt to keep this information secret?
If Apple felt it was morally “right” to have a back door why did they not point it out as a benefit that differentiated the iPhone from others by virtue of the fact that Apple could “protect” the end user from malicious code by virtue of said backdoor? Or in the case of the logging and reporting that I have just discovered, why is it not shown as part of the synchronization process? I mean, when you sync the iPhone to iTunes each step of the process is displayed: syncing addresses, syncing mail, syncing iTunes music, syncing photos… so why doesn’t it display syncing system performance data or syncing crash logs or even just syncing third party application information?
Of course the “why” is rhetorical. Apple doesn’t make this activity transparent to the end user because Apple doesn’t want the end user to know that it’s happening.
Further, the idea that I would have to submit to a violation of my privacy in order to have a telephone activated is simply absurd – providing a consumer with technology that he or she purchased should never give a company the implicit right to log information about what is stored on said device or how said device is being used by the consumer unless – and this is a very big “unless” – the company makes the end user conspicuously aware that such logging and transmission of this information is taking place.
Further, in the event that a company would still be willing to capture this information albeit with the consent of the consumer- they should take every possible precaution to make certain that no personally identifiable information is flowing back to the company or which could be intercepted by a third party at some point in the process.
Apple is clearly not doing this and is, in fact, very obviously capturing personally identifiable information including the IP address of the machine as well as the user name of the account holder. This of course ties (probably automatically) to Apple’s iTunes user database and from there they have everything including your credit card number and physical location and your billing address. How many people do you think WANT Apple to have all this detail about them? How long until Apple does what the carriers have been doing and gives this data over to the federal government for some more illegal spying on the population?
It’s somewhat amazing to me that more isn’t being made of this issue. With the uproar about the domestic wiretapping and other telco-based illegal spying that has gone on, I’m truly surprised that what Apple is doing isn’t national news. After all it’s not like there are only a couple thousand iPhones out there now. There are millions and millions – certainly enough that this is a large public interest story.
How Apple manages to continue to get away with this sort of bad behavior without so much as a spanking by the media really makes me scratch my head and wonder if the mainstream press is nothing more than a big bunch of syncopates all dancing to the beat of their corporate oligarchs.
There has to be a limit established beyond which a company simply has no right under any circumstances to gather data about me, my activities, my preferences or the contents of my personal files.
Remember that almost every contract has a provision that states that any tenet of the agreement to be found unenforceable does not invalidate the remainder of the agreement. Why do you think that is? Could it just be that it’s because companies know that they are pushing the boundaries of the law and are trying to protect themselves in the event that these boundaries prove less elastic then they’d hoped?
For me the bottom line here is simple. Apple needs to offer up a truly convincing argument as to why it is necessary to collect this information and they also need to show me that given that such a need really exists, that the information will be collected in such a way that it does not compromise my privacy or security or diminish in any way (including by taking up space that would otherwise not be used)the utility, value or my enjoyment of anything I purchase. Finally, Apple should be compelled to make this process known to the consumer, and patently obvious during any collection or transmission process.
If Microsoft has the courtesy to request permission to capture information about an application hang why can’t Apple act thusly as well?
Oliver
You’re looking at crash reports, and iTunes clearly asks you when you connect the device with said reports on it if it should submit them to Apple for you.
You’re reading a little more into this than is really there.
First of all, what you can see there are crash reports. They record information about a process which crashed, along with ancillary (non-identifiable) information about the state the device was in at the time. SOME of these MIGHT be submitted to Apple automatically, such as crashes in the modem baseband, because that’s a really big problem which they want to know about immediately. However, there’s nothing to say that the information has been sent to Apple.
Look at the information in those files; here’s an example from my computer:
Version=2
IncidentIdentifier=9D88F621-55A4-452D-8B21-8E3BBD639B85
Date=2008-12-22;AP=5G77;BB=02.28.00;Model=N82AP;Machine=iPhone1,2
12:40:31 -0500 ST [clm] disconnect: duration=178;cause=kNoError;ceer=0;txPower=-9;maxTxPower=0;rat=2;cgi=302:720:60010:18805
15:37:21 -0500 ST [clm] disconnect: duration=76;cause=kNoError;ceer=0;txPower=-13;maxTxPower=0;rat=2;cgi=302:720:60010:20114
17:50:23 -0500 ST [clm] disconnect: duration=152;cause=kNoError;ceer=0;txPower=-28;maxTxPower=0;rat=2;cgi=302:720:60010:18446
I don’t see any identifying information there. I just see a record of baseband connection failures. No logging of the call I make or the apps I’ve installed. And I only see them recorded fairly sporadically, too.
Now look at the information in your screenshot. Do you really think there’s something vulnerable in there? The only app you’re running is NYTimes, an app I’ve been told is prone to frequent crashes. It doesn’t look as though you’ve got any ‘evil hacking programs’ running, so it looks like the crash was legitimate in nature. Note that this file is NOT sent anywhere, it’s just stored somewhere you can reach it should you request support from the NYTimes app authors.
The other items in there are crash logs. That’s all, just crash logs. They list a stack backtrace of all threads in the app that crashed, in non-symbolified format (i.e. it’s a list of addresses, not function names). Those don’t get sent anywhere, but they do get copied to your Mac because, well, how else are you going to be able to send them to the developers to get the crash fixed? Telepathically read the data from the iPhone?
The console log, which records anything that applications choose to log for informational or debugging purposes, appears to be completely unavailable outside of using the Xcode development tools to access it directly from the (tethered) iPhone. This in particular is making my job difficult right now, because I need to see if any errors were logged on a user’s iPhone, but I can’t find that out. He’s not getting a crash, so there is no information stored anywhere that he can provide to me.
In short: it’s all your data. Delete it from your computer if you don’t like it, but things like crash reports and backed-up data needs to be stored somewhere, and your computer is the right place, no? As opposed to sending it somewhere outside your reach?
how did you get your console to display this?
Alan,
Thanks for the thoughtful reply. I am well aware that the segment of my console logs that I provided to demonstrate the issue was simply that of application hangs and crashes. However, this is merely a snapshot of the logs and doesn’t include any of the more sensitive information that was captured nor did the image include the portion of the logs that identifies what has actually been “submitted” somewhere…
The word submitted actually appears multiple times in the logs and I cannot imagine that such a term is there for no reason. Further, it was obvious to me that the ip address and other identifying information was also captured. Please don’t assume that because I preface the article with the statement that I am not a developer that this also means I am not technical.
I’ve been using computers since 1976 and know a number of programming languages. It has simply been quite some time since I was actively involved in actually writing anything more involved than web pages or CMS template revisions. That said, having been a systems administrator for more than a decade I’ve seen my share of log files across a large array of machines and OS’s and I am confident that the information that I reviewed on the log that was the impetus for the original post did indicate capture and transmission of information that I did not agree to share with any third party least of all information being transferred from one device to another and then transmitted without my knowledge using an internet connection that I pay for.
So, while I don’t disagree at all with your contention that the data does have a use and that collection on my computer is probably the best location for that data to be stored, what I still have a problem with is the fact that Apple has done this collecting and worse the transmission back to base without disclosing that this was taking place or asking my permission to collect this information in the first place..
Oliver Starr
Well, sure, we should all read the license agreements when we buy software or services. But really, what choice does one have when faced with “Do I activate my iPhone that I already bought and need for my job?”.
I don’t have a problem with my iPhone phoning home, though.
Your claims would carry more weight if the screenshot you provided as evidence actually displayed some of the malicious behavior you’re describing. A set of crash dumps containing callstacks and lists of active processes (active as in running at the time of the crash, not the set of installed apps) is exactly what I’d expect to find in the console log.
Also, the first time I connected the iPhone after such a crash, iTunes asked me whether it had my permission to submit the crash data to Apple. Did you not receive the same notice? The message contained a “Don’t ask me this again” checkbox, so now such events are submitted automatically.
I realize this may be moot but I’ll say it anyway. There are MANY more cases of the iPhone disclosing personal information without the users consent or knowledge. IEMI, serial#, phone #, GPS coordinates, etc. are all personal and private as far as I’m concerned.
The crash logs are nothing. If you want more serious examples, try watching the phone over wireless with tcpdump (or whatever you choose). It astounds me that people are using these devices.
Some gems:
– Using apples Weather App, look at the weather for your area and note the phone does a post with your IEMI _after_ receiving the forecast.
– The phone will frequently (and for no obvious reason), ping various apple assets including
– http://iphone-wu.apple.com/7day/v2/latest/lto2.dat
– http://www.mac.com
.. etc.
Hell, I setup an email account and saw the phone grab some file from apple.com.
I’m not a crazy nut, I’ve SEEN and have logs (dumps) showing the phone doing this even without jailbreaking.
If you don’t believe me, try for yourself. If you have the ability to do so, I’d highly recommend setting up a pix and using the cisco vpn client on the phone. Then watch the fun (especially while roaming/not over wireless).
I’ve no idea what the phone does over the carriers network but I suspect the same if not worse.
Don’t even get me started on cydia either. If people had ANY idea what those applications really do in the back, the iPhone wouldn’t be allowed any where near a corporate network. It isn’t what you can see, it’s what you can’t or refuse to.
And no, I’m not for apples Killswitch, which is what I think apple is waiting to justify its use on.
Pingback: Grill restaurant - Bar grill - Bar chilis grill restaurant